Case Study: Assured [Core] - How Brampton SMB Protected Data from Cyberattacks
The best practices for securing the cloud and protecting sensitive data.
![Case Study: Assured [Core] - How Brampton SMB Protected Data from Cyberattacks](https://cdn.prod.website-files.com/6740cdf27c0178381c0c1f50/6740cdf27c0178381c0c1f5e_securing-the-cloud-thumbnail-v1-cybersecurity-x-webflow-template.png)
Case Study: How a 2-Day Assured CORE™ Sprint Transformed a Mortgage Brokerage’s Cybersecurity Posture
Client Overview
A regional mortgage brokerage firm serving over 200 active clients relied heavily on digital operations — from online loan applications and client document uploads to cloud-based CRMs and shared drives. Yet, like many SMBs, they had minimal cybersecurity controls in place.

The Challenge
Before partnering with Security Assured, the brokerage faced:
- No MFA or password policy enforcement on email and CRM.
- Publicly exposed website admin panel and outdated CMS plugins.
- Unsecured file-sharing for client financial documents.
- Laptops running outdated antivirus software and no EDR.
- No incident-response plan, security policy, or backup verification.
Their cyber-insurance provider had also flagged them as “high risk,” jeopardizing renewal.
The Assured CORE™ Sprint – “48 Hours to Secure”
Security Assured deployed its Assured CORE™ 2-Day Sprint — a rapid-action service designed to harden small business environments within 48 hours.
Day 1: Discovery + Defense
- Conducted rapid baseline audit of email, endpoints, and web assets.
- Implemented MFA across Microsoft 365 and CRM accounts.
- Hardened email with SPF/DKIM/DMARC.
- Patched CMS vulnerabilities and locked down the admin portal.
- Configured secure file-sharing with encryption and access logs.
Day 2: Backup + Behavior
- Verified backup integrity and performed a restoration drill.
- Deployed lightweight EDR on all endpoints.
- Delivered an “SMB Cyber Hygiene Kit” — tailored policies and playbooks.
- Conducted micro-training and a phishing simulation for staff.
- Built a 90-Day Cybersecurity Roadmap with prioritized next steps.
Measurable Results (Within 72 Hours)
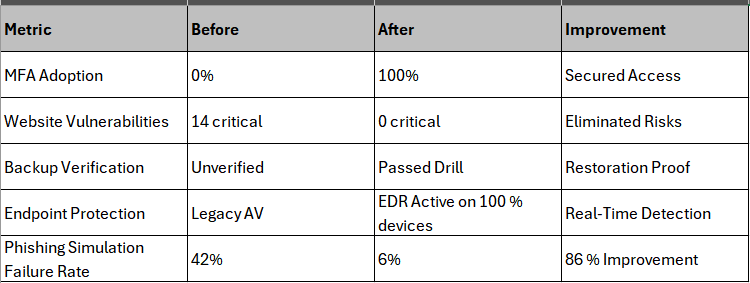
The brokerage’s cyber-insurance renewal was approved with a premium reduction, and they received positive feedback from underwriters citing “clear evidence of improved controls.”
Client Testimonial
“In just two days, Security [Assured] turned our cybersecurity around.
We went from uncertainty to confidence — our website, devices, and client data now feel protected and professional.”
— Operations Director, Mortgage Brokerage Firm
Key Takeaways
- Speed matters. A focused 48-hour sprint can dramatically improve SMB security posture.
- Visibility drives confidence. Measurable metrics make cyber risk tangible.
- Readiness wins deals. Strong controls directly influenced insurance and client trust.
Ready for Your 2-Day Sprint?
Your business can achieve the same overnight transformation.
Visit https://www.securityassured.ca/company-pages/assured-core or call 365-777-0000 to schedule your Assured [Core] Cybersecurity Sprint.
Subscribe to our weekly newsletter
Get the latest cybersecurity trends, threat updates, and AI security insights — weekly.





